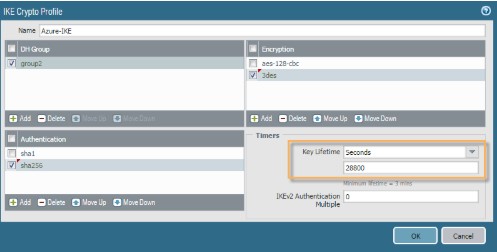
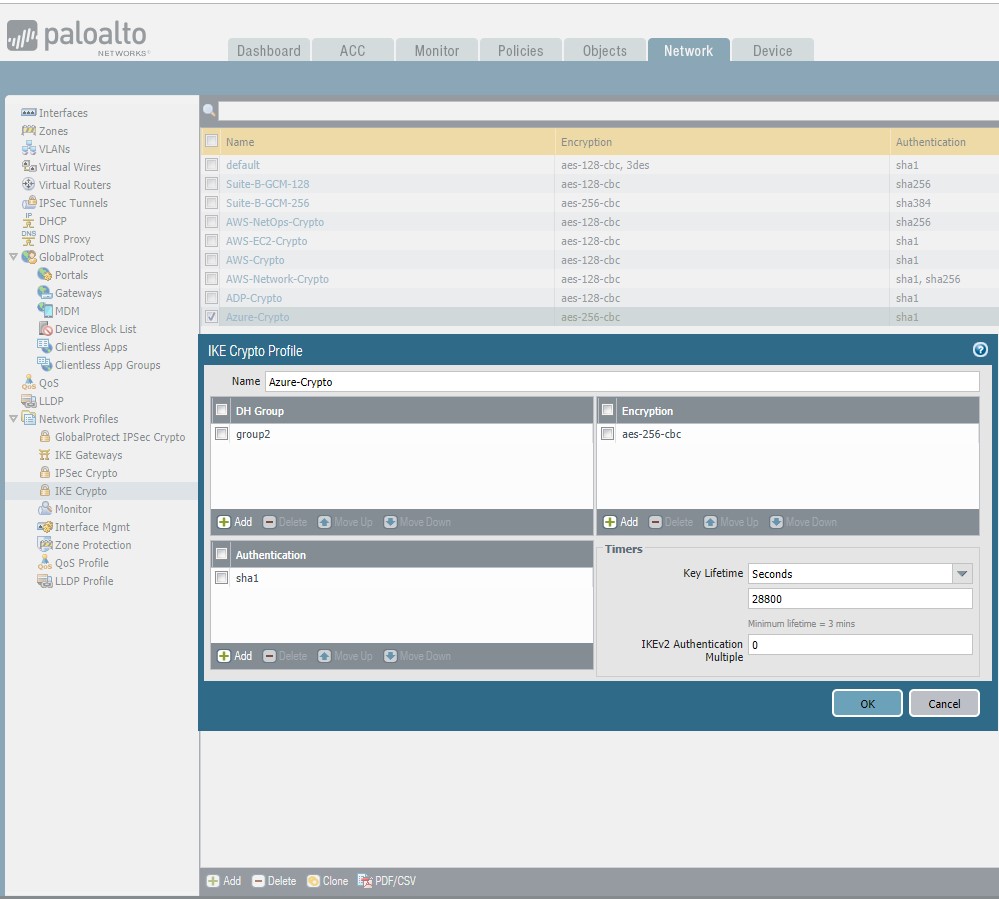
Situation: The client configured their Palo Alto firewall connecting to Microsoft Azure site to site VPN. However, it shows “Connecting” forever.
Troubleshooting: It is preshare key problem. We fix it by running these commands:
PS C:\Users\blin> add-azureaccount
Id Type Subscriptions Tenants — —- ————- ——- chicagotech.net@gmail.com User 3d083292-8d49-4ef7-8c72-e54522b52126 {488899b5-4a4a-48b1-a1cf-8a1229d32267}
PS C:\Users\blin> Select-AzureSubscription -SubscriptionId 3d083292-8d49-4ef7-8c72-e54522b52126
PS C:\Users\blin> Get-AzureVNetConfig -ExportToFile “C:\Users\Public\Downloads\networkconfig.xml”
XMLConfiguration —————- …
PS C:\Users\blin> Set-AzureVNetGatewayKey -VNetName ‘Group TestVPN Test’ `
>> -LocalNetworkSiteName ‘498DEBEF_AzuretoOnprem’ -SharedKey asjdfojweioreroihew
Error : HttpStatusCode : OK
Id : b0f50fe7…..
Status : Successful RequestId : ea98d58a3b75a8bf96….