- Try ping or trace route command to rom the PA external interface to the peer’s external interface.
- Make sure that the IKE identity is configured correctly and matches.
- Check that the policy is in place to permit IKE and IPSec applications
- Some useful commands:
a. show vpn ike-sa gateway <name>
For example:
show vpn ike-sa gateway Azure-Gateway
b. test vpn ike-sa gateway <name>
For example
test vpn ike-sa gateway Azure-Gateway

c. show vpn ipsec-sa
d. show vpn ipsec-sa tunnel <tunnel.name>
For example
show vpn ipsec-sa tunnel ipsec-tunnel-3
e. show vpn flow name <tunnel.id/tunnel.name> For example
show vpn flow name ipsec-tunnel-3
f. test vpn ike-sa

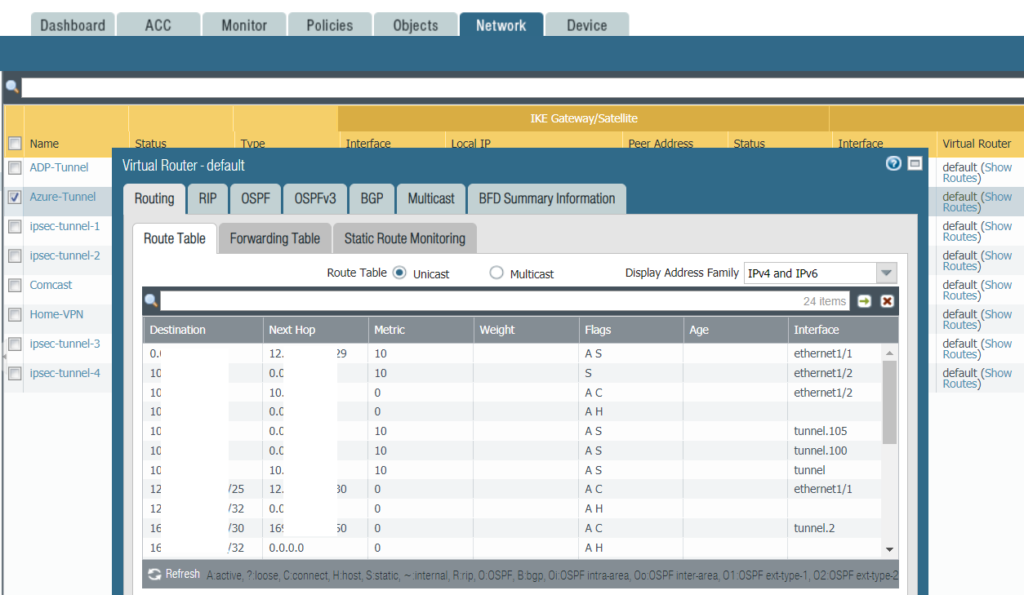
5. Check GUI
a. Go to Network>IPSce Tunnels. Mkae sure all Status are green.
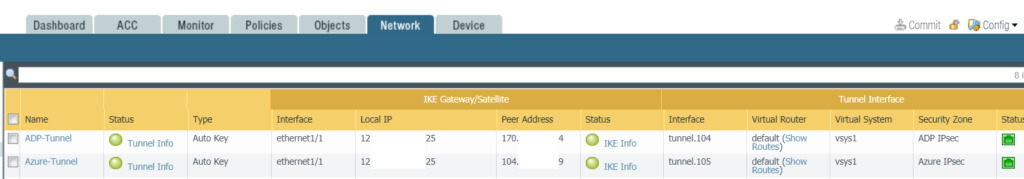
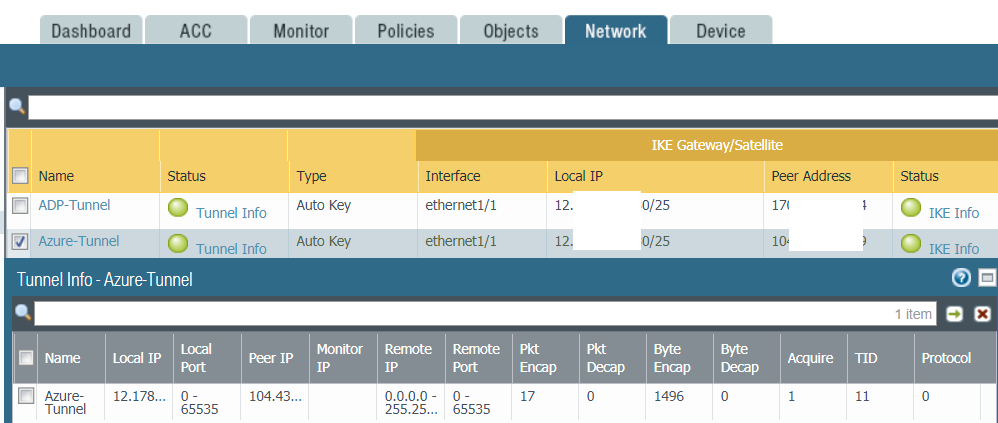
b. Go to Network>IPSec Tunnels. Check Tunnel info.
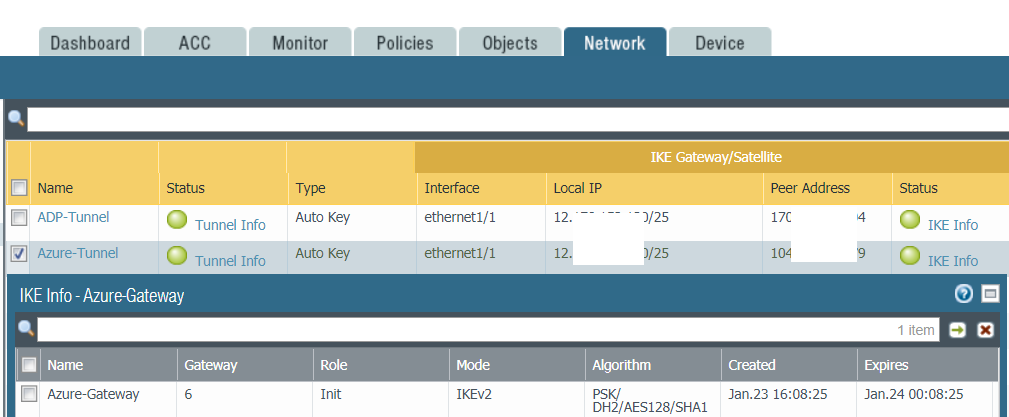
c. Go to Network>IPSec Tunnels. Check IKE info.
d. Go to Network>IPSec Tunnels. Check default (show routes)
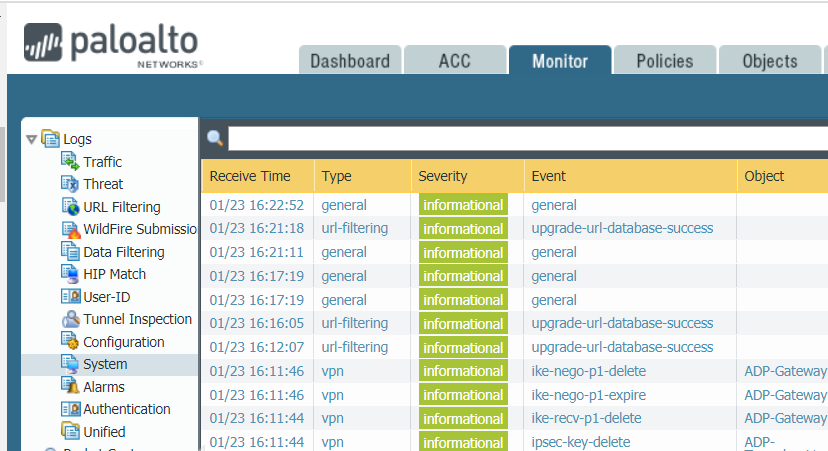
e. Got to Monitor>Logs>System to check any errors.