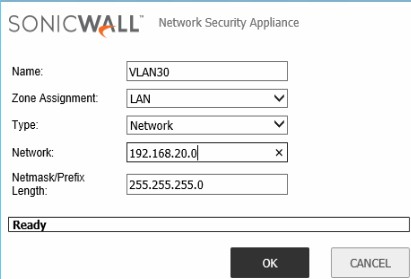
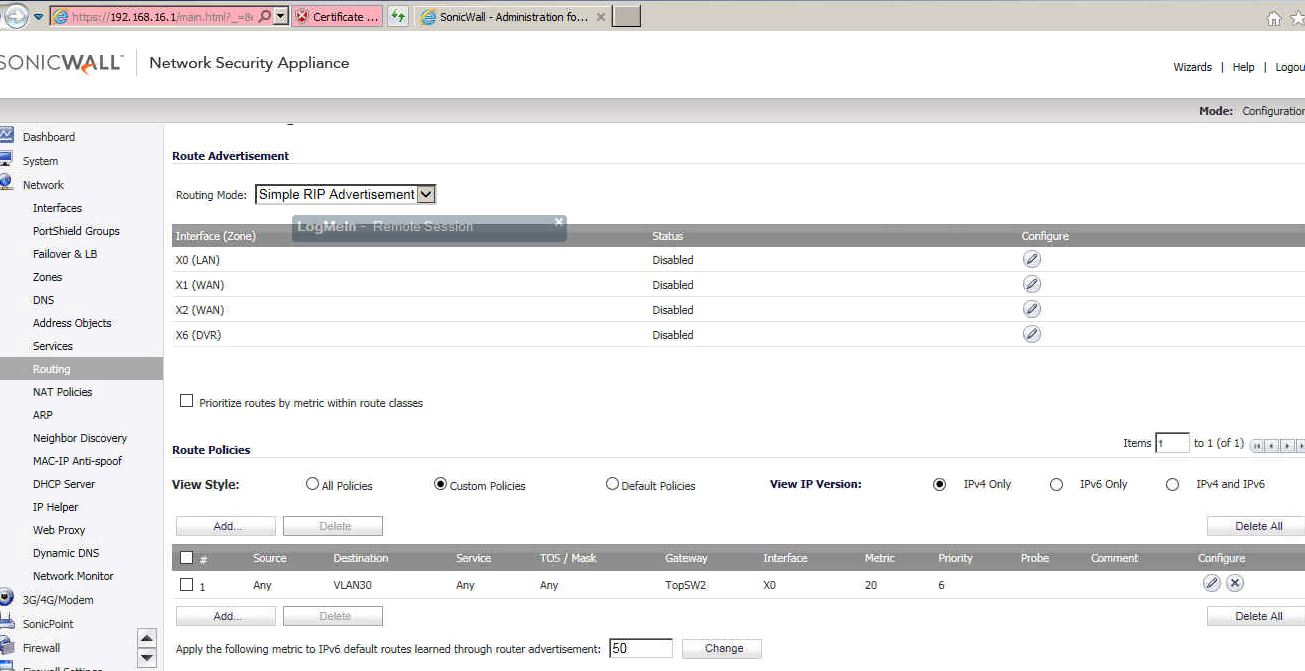
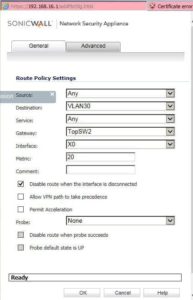
Situation: the client created VLANs in their network and configured routing on SonicWall, but the routing doesn’t work and VoIP VLAN can’t access the Internet and data VLAN can’t access the VoIP VLAN.
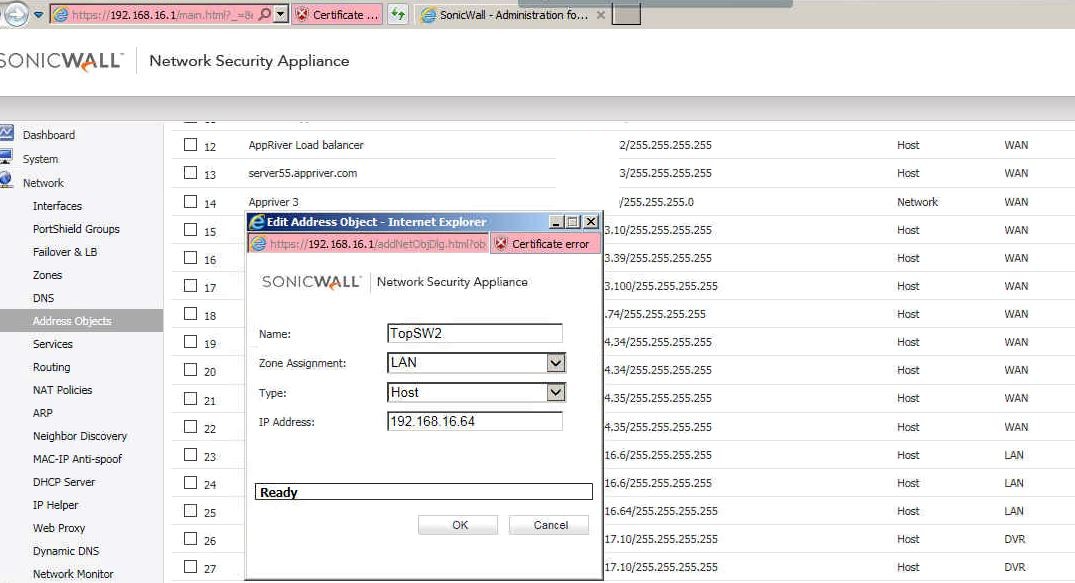
Troubleshooting: The gateway they tried to add for the routing policy is using VLAN VoIP Ip address (192.169.20.1) on the switch instead of data VLAN IP address (192.168.16.64).
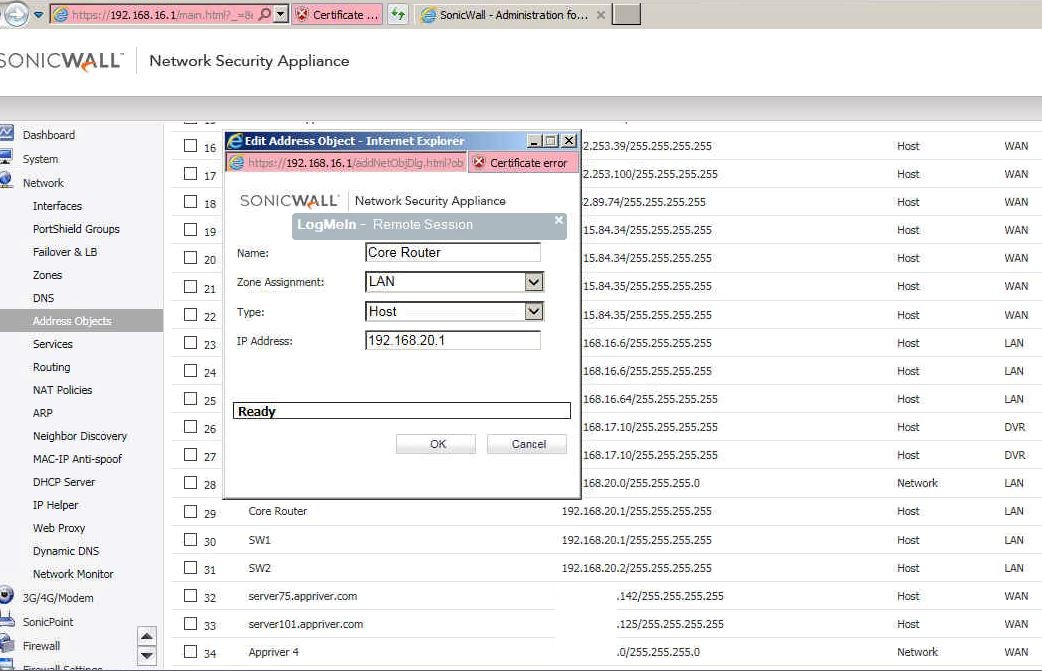
Since the default gateway is in the data VLAN (192.168.16.1), we create a new network object using switch data IP address (192.168.16.64) and replace the IP address 192.168.20.1. That fixes the problem
More details can be found this link: How to configure routing on SonicWall